NFL Advances In-Stadium Wireless Connectivity
(Image courtesy of www.sportsauthorityfieldatmilehigh.com) With the NFL season kicking off, we decided to investigate one of the more overlooked aspects of the game: in-stadium wireless communication. Surprisingly, several aspects of the game experience rely heavily on wireless communication: coaches headsets on the field and in the booth, concession stand payment processing, and, of course, fans with smartphones. Anyone who has attempted to connect to publicly available wireless internet in a stadium, concert venue or otherwise generally crowded area knows that connectivity is finicky at best and nonexistent at worst. In the era of instant score updates, fantasy leagues, Twitter and other social media applications, fans expect to be able to use their smartphones during a live-game experience. Additionally, even just a few years ago coaches themselves dealt with connectivity problems: … The tablet computer in his left hand — a high-tech replacement for the black-and-white printed pictures coaches have used for decades to review plays — kept losing its Internet connection, leaving Belichick unable to exchange images he and his coaches rely on to make in-game adjustments. The fault is apparently in a new private Wi-Fi network the NFL installed in stadiums this year to great fanfare. Internet service is erratic, making a system financed by one of the world’s richest sports leagues little better than the one at your local coffee shop. … Of course, since then, the NFL has gone out of its way to better incorporate wireless communication technology into the stadium experience for fans and personnel alike. This year, the Denver Broncos 3,000 5 GHz wireless antennas in Mile High Stadium (we should note, the claim of ‘most of any NFL venue’ is unverified): To increase fan connectivity, Broncos announce install of 3,000 5GHz wireless antennas at stadium, believed to be the most of any NFL venue. pic.twitter.com/ES2CWZhJ0z — Patrick Smyth (@psmyth12) September 5, 2017 For the NFL, and other large events, the question of connectivity has more to do with bandwidth capacity than access to a wireless network. Most cellular carriers provide access to LTE networks in the populated areas where stadiums and event centers are located, but the sheer amount of data being used during an event like the Super Bowl has grown exponentially over the years. In 2014, data usage at Super Bowl XLVIII totaled around 2.5 terabytes. Super Bowl LI, played in February 2017, saw nearly 12 TBs transferred throughout the game over WiFI alone, with Facebook and Snapchat accounting for almost 10 percent of the total bandwidth. Verizon and AT&T customers combined to use another 20 TB of data over those networks. With those numbers in mind, it makes far more sense to utilize high-bandwidth technology like WiFi, rather than relying on the LTE networks to support those big data figures. When IIoT and the NFL Collide The average consumer thinks of WiFi as a broadband service facilitated by a router in one’s home or office. When scaled to the usage size of a football stadium-worth of bandwidth consumption, however, a regular router will not suffice. Instead, these stadiums use wireless communication technology that has been deployed with regularity in the Industrial IoT for years: signal repeaters and access points peppered strategically throughout the necessary coverage areas. Just like companies in the utilities, oil and gas, precision agriculture and smart city industries, these stadiums are relying on industrial-strength WiFi platforms to handle the data demands of teams, vendors and fans. An additional consideration for stadiums and critical industries is the security of these networks, so tech vendors must be able to supply built-in security measures within the access points. These networks must be secure, flexible and reliable in order to support the massive demand being made for hours on end. The New Generation of Stadium Experiences We tend to take internet access for granted these days. Connectivity is already nearly ubiquitous and only growing each year, so it makes sense that stadiums would eventually start to catch on to the technology being used to propagate these industrial-strength networks. At this point, it is not just the NFL that is working on pushing the stadium experience into the next generation, other professional sports leagues, music venues, and festival sites are catching up to the IIoT technology that is proving to be a literal game changer.
Rugged Wireless Radios for International OEM Applications
For original equipment manufacturer (OEM) and military applications around the world, operational success requires reliable data delivery. This 100 percent achievable with rugged wireless radio solutions. As Industrial IoT pushes for more connectivity, coupled with the surge in commercial use of unmanned aerial systems (UAS), the pressure for around the clock command and control (C2) links is higher than ever – and it’s happening on a global scale. To support these growing needs, FreeWave has announced the general availability of the MM2-5 Watt 1.3 GHz (13X5W) integrated radio. Offered in a small package for ease of integration, the MM2-13X5W features an external 5 Watt output, making it ideal for UAS, OEM and military applications where reliability is paramount and space is at a premium. These solutions can be leveraged to deliver important data in the U.S. and abroad for a wide variety of mission critical applications. The MM2-13X5W has a lot to offer starting with it’s built in versatility and the ability to function as a gateway, endpoint, repeater or endpoint/repeater. Security is a priority – each MM2 13X5W is equipped with proprietary frequency hopping spread spectrum (FHSS) technology. It also features a line-of-sight range of up to 90 miles, and can be deployed in international settings where lifesaving communications and security are paramount. A number of these use cases include UAS applications, soldier training, environmental monitoring and other government and defense needs. Next Generation UAS Applications As the commercial drone market rapidly expands, the number of use cases is filtering into new markets. Beyond the military scope, commercial UAS applications have the potential to completely transform the monitoring, control and data analysis processes for many industries. The MM2-13X5W is equipped to support this next wave of these UAS applications, including: Pipeline monitoring as a service – drones can help maintain safe and consistent visibility of the pipeline and deliver that critical data to the network. The small form factor and proven reliability means uninterrupted data transmission in remote settings. Homeland security apps – recently, in the U.S., there have been many heated conversations around border protection. Many drone supporters believe that UAS can offer a cost effective way to monitor the nations borders. The U.S. border patrol even recently solicited contractors to build facial recognition drones. Drone delivery service – As we look at the future use of commercial UAS, drone delivery is a popular topic of conversation. We’re also seeing use cases where drones can deliver food and medicals supplies to high risk areas in third world countries. Precision Agriculture: Drones can enhance crop visibility, enabling smarter decisions and more food output. The potential impact of drones in precision agriculture is becoming recognized throughout the world. As the possibilities for commercial UAS continue to multiply, so does the need for secure C2 links for successful operations – and this is where the MM2-13X5W is an ideal solution. Additional Product Features The MM2-13x5W also features the following: 115.2 and 153.6 kbps selectable RF data rates TDMA, Super Epoch TDMA, and AES Encryption Performance tests from -40 degrees Celsius to +85 degrees Celsius Data link range up to 90 miles For more information about the MM2-13X5W, please visit: https://www.freewave.com/mm2-m13-series/
The Importance of Frequency Hopping
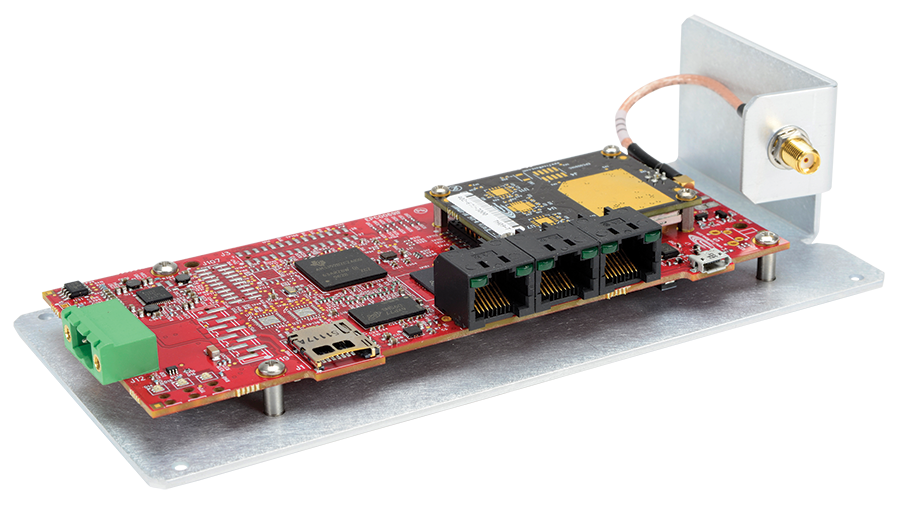
(Original blog can be found on the Texas Instruments website) Are you a fan of those 1940s black-and-white movies where a damsel in distress gets rescued by a rough-and-ready private eye? If so, then you’ve probably seen actress Hedy Lamarr. In real life, Hedy was no damsel in distress. She was one of the primary inventors of frequency hopping technology now seen in Wi-Fi®, Bluetooth® and code-division multiple access (CDMA). The technology Hedy Lamarr helped invent is frequency-hopping spread-spectrum (FHSS) radio technology. FHSS is a wireless technology that spreads signals over rapidly changing frequencies. Each available frequency band is divided into subfrequencies. Signals rapidly change, or “hop,” among these subfrequency bands in a pre-determined order. Used in global industrial applications for over 60 years, 900MHz FHSS radios equipped with TI’s chipsets like the SimpleLink™ Sub-1 GHz CC1310 wireless microcontroller (MCU) now have the ability to host process-automation apps for the intelligent command and control of remote sensors and devices. Without having to leverage expensive Wi-Fi bandwidth, lay fiber or employ cost-prohibitive cellular, companies can now take advantage of proven low-power FHSS technology to automate processes at the network edge. The proliferation of smart sensors and high-bandwidth devices makes low-power FHSS technology a viable and cybersecure wireless data option for oil and gas, unmanned systems (like unmanned aerial vehicles [UAVs] and robots) and original equipment manufacturer (OEM) wireless integration. Because innovators like TI have developed such powerful chips, FHSS is no longer restricted to pure telemetry or input/output (I/O). Indeed, FHSS increasingly supports voice and video, and can scale to form self-healing mesh networks. Moreover, FHSS transmits data over much longer distances than Wi-Fi, Bluetooth, LoRa or zigbee – up to 60 miles in some cases. Because FHSS is a wireless technology that spreads its signal over rapidly hopping radio frequencies, it is highly resistant to interference and is difficult to intercept. Interference at a specific frequency only affects the transmission during that extremely short interval, making FHSS inherently cybersecure. By employing intelligent TI-based FHSS technology, organizations can take advantage of real-world fog computing and intelligent edge communication devices that are cybersecure and resilient. When deployed as process-automation nodes, these devices (pictured in Figure 1) can make decisions and take action at the access level (or at the sensor or device). Indeed, not only is FHSS a reliable and robust option for Internet of Things (IoT) networks, it is also a low capex and opex solution that can work for years without maintenance. Contact FreeWave to learn more about FHSS technology and order a couple of TI-powered radios that you can program (in Python, Node-RED and Node.js) for real-world fog and edge applications. Also, find out more information about the CC1310 wireless MCU and other products within the SimpleLink MCU platform.
Manufacturing in the Age of IIoT
Few industries can claim such a foundational impact on the United States as the manufacturing industry. Modern manufacturing began with the birth of the assembly line and the transformational effect it had on the automobile industry. Companies then adopted that approach to product manufacturing and logistics. The early phases of the next generation of manufacturing appeared as machine-to-machine (M2M) communication, a forbearer of the concept behind the Internet of Things (IoT). Eventually, IoT became so broad that specific designations were needed to differentiate between the consumer and industrial side of things, thus paving the way for the Industrial IoT (IIoT). Today, manufacturing companies, while often on the leading edge of automation technology, are still scrambling to adapt to the explosion of sensors, communication platforms, big data and high-speed analytics to maximize efficiency and future-proof their products or designs. Some companies are touting the idea of retrofitting – a concept that has existed for some time – but some plant engineers may be wary of the need for continual updating to a system that is bound to become irrelevant at some point. Still, the process can be relatively painless, and is quickly becoming necessary, as Plant Magazine notes: … Most food manufacturing and processing plants have motors powering essential equipment such as mixers, conveyors and packaging machines. But they’re just motors. They don’t play in the same league as other intelligent devices. With years of service to go, it’s difficult for plant managers to justify replacing motors that work just to make an upgrade with smart features. But motors can connect to the IIoT without a complete overhaul. Instead of investing in new, more intelligent/smart equipment, consider investing in sensors that provide similar functionality to connected devices. Smart sensors attach to almost any standard low-voltage induction motor. Sensor technology is sophisticated enough to be small, functional and energy efficient. For certain kinds of manufacturing plants, a complete overhaul may not be necessary, and a ‘simple’ retrofitting process might easily solve the first part of the problem. The second part of the problem, or challenge, is that along with smart hardware, plants also need the software and data processing capabilities to keep pace. Some plant engineers are solving these challenges by deploying programmable radios capable of hosting third-party applications so that the data can be transmitted in smaller, highly specific packets, making the transport both fast and easier to push into predictive analytics platforms. From there, software companies are building in the ability to process data in the cloud, essentially running all critical data and software operations through either a fog or cloud computing process. Cloud software services have the potential to be highly customizable based on the needs of the manufacturing plant. These technologies are good examples of the ongoing convergence between traditional information technology (IT) and operations technology (OT) needs in industrial markets. Currently, the manufacturing industry is sitting in an interesting spot: leaders in the M2M world, but still adapting to the IoT world. Where the industry ends up in the next 10 years could be a strong indicator of the economic and financial temperature of the domestic and international marketplaces.
7 Tips for OEMs to Improve SCADA Networking Communications
From remote field sensors to Supervisory Control and Data Acquisition (SCADA) and I/O modules, industrial wireless radios connect your device and sensor ecosystems with robust and reliable links. Furthermore, wireless data radio networking technology connected to I/O modules for SCADA applications have become faster, smarter and their firmware now easier to upgrade. More options and frequencies, including 2.4 GHz for short range I/O and 900MHz for long range data networking, continue to improve SCADA-based network communications for robotics, industrial automation, unmanned systems and heavy machinery. So what do Original Equipment Manufacturers (OEMs) need to know when deciding upon which technology to use? Below are seven tips for OEMs to consider when reviewing industrial wireless communication options. 1) Assess Technology Options for the SCADA Network Start first by identifying your needs, goals, and limitations. When it’s time to research technology options, observe what’s available today and what’s going to be available in the future, heeding the “buyer beware” saying. Communication products vary in many ways, and each manufacturer and/or technology has advantages and disadvantages. No single product—and likely not a single manufacturer—can meet all application needs. 2) Reduce Costs While some companies seek to continue to preserve existing investments of wired and wireless technologies, wireless options have clear advantages for SCADA systems. Most obviously, wireless installations reduce labor and material costs by avoiding hard-wiring remote assets. Speed of deployment adds savings. Wired systems can take days or weeks to be properly installed. Wireless networks generally require only the end points to be installed, saving substantial time and costs. Networks need to scale gracefully as the number of end points increases. After installation savings, scalability is the biggest advantage of wireless over hard-wiring, including slow integration into wired systems as it’s implemented. 3) Consider Hybrid Benefits Toss out any old perceptions. If you need mobile SCADA network access, find somebody that offers it. If you have a microwave tower place, use it. Piggyback slower licensed radio networks with faster 902-928 MHz frequency hopping, AES encrypted networks. Know that you can install I/O capable radios (analog and digital signal, 4 to 20 and 1 to 5) to relay contact closures or other data without adding a new Progammable Logic Controllder (PLC) or Remote Terminal Unit (RTU). 4) Maximize SCADA System Value With telemetry technologies, such as spread spectrum radios, the same radio used in RTUs can act as a slave device sending data back to the SCADA host, and as a repeater to other field devices or other RTUs. This allows almost limitless network expansion by using remote sites as a series of repeaters, and by using radios in the RTUs to poll the instrumentation. Polling the instrumentation creates a second network reporting wirelessly back to the RTU. This shorthaul network is the equivalent of a local area network (LAN). 5) Don’t Use a Proprietary SCADA System By using a non-proprietary SCADA system, users gain real-time access, control, and monitoring of their network (including all the devices and functions of their network). They can manage requirements of an ever-growing system allowing them to manage their network in real-time with fewer bodies and hours invested. Security and safety improves with better monitoring. For instance, some industrial systems don’t contain a process for monitoring the cathodic integrity for corrosion (like in water/wastewater and oil and gas) to avoid disaster. But with deployment of a wireless system, they can. They can begin by monitoring simple things, such as pump stations at wells, using I/O radios communicating back to the central SCADA system to get up-to-date information on the tanks’ or pipelines’ status. End users can more quickly resolve an emergency wirelessly, instead of manually. 6) Seek SCADA System Flexibility Advanced flexibility of radio communications offers benefits to new SCADA system deployments and upgrades performance of existing SCADA systems. For example, in water/wastewater industrial applications, there need to be generation/distribution, lift stations, system monitoring, and treatment facility systems in place (or planned) to meet the expanding growth of a community’s population and/or service areas to meet future requirements. Each year, many industries deploy more frequency hopping spread spectrum (FHSS) SCADA solutions to help monitor and manage critical infrastructure. Several manufacturers (including FreeWave Technologies) offer FHSS radios capable of retrieving data from remote locations. And although wireless IO (input/output) has been available, only recently have both capabilities been offered in one communication solution. 7) Seek Easy-to-Use SCADA Software OEMs implementing and using a SCADA network systems for data communications want a simplified, rapid setup and easy management of a network. That includes ability to manage multiple frequencies and multiple networks within one system. A centralized storage and management center provides easy access to system configuration and diagnostics data. Technicians in remote or harsh weather environments need robust reporting capabilities. Software like FreeWave’s ToolSuite can manage data communication diagnostics and configuration.
A ‘Heads Up’ on Drone Safety
We all know that what goes up must come down. In the case of drones falling out of the sky, hopefully your head isn’t in the collision path. Drones are becoming increasingly popular for commercial and recreational purposes. According to a recent FAA report, this has sparked an “increase in accidents resulting in blunt impact or laceration injuries to bystanders.” The report, released late last month, generated a fair share of news coverage. It examines the dangers of drone collisions with people on the ground, the risk of injury and ways to reduce those risks. The good news, and probably most newsworthy conclusion, is that if a small drone were to hypothetically fall from the sky and collide with your head, you probably won’t die. One of the tests conducted during the study included dropping a drone on the head of a crash test dummy. The drone used in the test represented a typical drone — a Phantom 3, which weighs about 2.7 pounds. Test results determined that a drone causes significantly less damage than a wood block or steel debris. Findings also showed that the “drag,” caused by air resistance slowed the drone down much more than the wood and steel. A USA Today article reported that while there was only a 0.01 to 0.03 percent chance of a serious head injury, but there was an 11-13 percent chance of a serious neck injury. While the risk of serious injury might be lower than expected, both drone manufacturers and operators of remotely piloted aircrafts can continue to actively take responsibility for the risks by operating from a preventative and safety-focused perspective. A combination of proper training, education and reliable, secure command and control links (C2) can lead each side to a safer drone environment. Knowing the Rules Groups have formed with commercial drone safety in mind. Know Before You Fly is an organization dedicated to educating drone operators on the FAA guidelines for operation. They also offer resources on how to safely and responsibly operate unmanned aircraft systems (UAS). The FAA report also names Academy of Model Aeronautics (AMA), Association of Unmanned Vehicle Systems International (AUVSI), and the FAA as groups dedicated to educating hobbyist and commercial UAS users on the important requirements for piloting UAS. New drone operators who leverage the assortment of educational tools available can help champion the pursuit of responsible drone operations. Building Drones with Reliability and Safety in Mind In addition to training and education from the operator perspective, when the right command-and-control (C2) solution is in place, drone operations can become much more safe and reliable. Secure wireless data communication solutions that leverage data encryption capabilities, adhering to FIPS and AES standards, are already heavily relied on for mission-critical government and defense applications. Additionally, certain types of wireless solutions, like Frequency Hopping Spread Spectrum Technologies (FHSS) are secure in their nature. For example, frequency-hopping techniques can leverage coordinated, rapid changes in radio frequencies that literally “hop” in the radio spectrum, thus evading detection and the potential of interference Some wireless products also can deliver multiple user-defined cryptography keys (as many as 32 user-defined keys in some cases), providing more robust link security by allowing the automatic and frequent changing of cryptographic keys. In addition to secure data, these solutions also offer distance. There are FHSS radio solutions that can transmit more than 60 miles Line-of-Sight (LOS). When the communication links are robust and prevent interference, they are much less likely to be jammed or disrupted, ultimately preventing drone performance issues (i.e., falling from the sky). This is a very important consideration because of the growing number of unmanned vehicles operating in industrial and commercial sectors today. With a secure and reliable wireless C2 link, these technical issues are substantially reduced. Drones have opened the door for many hobbyist and commercial opportunities, but that also means there are more inexperienced operators. If an operator educates themselves on the FAA guidelines and safety procedures when operating a drone, and the manufacturers build in a secure and reliable C2 link that works over long distances, then both are taking the steps to decrease drone-related injuries. Although the FAA report shows the risk of serious injury and death is low, manufacturers and operators still need to keep safety a top priority.
2017 IIoT Prediction Series, Part 1: Where the Fog Meets the Edge
As 2017 kicks into full gear and a particularly interesting 2016 fades into the rearview mirror, we took a look around the IIoT landscape to see what this year might potentially have in store. We will be unveiling five IIoT-related predictions throughout this week and into next, so stay tuned and let us know what you think! It’s become increasingly difficult to ignore the importance of cybersecurity. From the role it played in the 2016 presidential election to the recent revelation that in 2013, more than one billion Yahoo accounts were breached, cybersecurity is no longer a problem unique to Sci-Fi thrillers. Of course, the two examples mention here are simply the most egregious of recent memory, but they pale in comparison to the threat of a cyberattack on actual infrastructure. Cybersecurity for the Industrial Internet of Things (IIoT) began as a minor headache and quickly grew into a full-blown migraine. Data is the perhaps the most important “currency” in the world today, and companies both public and private are scrambling to figure out the best way to protect that data will still ensuring real-time transport and analytics. With that in mind, our first prediction for the new year centers on the deployment of new methods for data transport and protection: 2017 will see the emergence of True Fog Computing and Programmable/Intelligent Edge Devices with the strongest security measures to-date. According to analysts, organizations have become more comfortable hosting critical infrastructure and application in the Cloud. In efforts to further optimize processes and shorten response times, organizations will explore ways to host applications at the device/sensor level (i.e., the Edge or Fog Computing). A decentralized network architecture that brings computing power closer to where data is generated and acted upon, Fog Computing enables analysis, control and automation closer to the “Things” in the Industrial Internet of Things. Because Fog Computing reduces the amount of data being sent to the Cloud, cybersecurity will be enhanced by reducing the threat and attack surfaces of IIoT networks. In industries where even milliseconds are vital, certain processes will move away from the Cloud and closer to the Edge. The basis of this shift in intelligence deployment is simple: the Cloud, while fairly secure, is still prone to security breaches, so rather than host all of the data and the analytics tools, move those processes closer to the edge to the sensors and devices with security already built in. Now, while the concept is simple, the execution is more difficult. This shift requires a robust, high-speed network capable of real-time data transmission and, perhaps even more importantly, programmable devices at the edge. Rather than thinking about big data from the perspective of drinking from a fire hose, a programmable device at the edge allows the user to develop proprietary applications that filters out unnecessary data. Subsequently, the smaller data packets enable two things to happen: faster transmission to the analytics engines, and the ability to send that data via mesh networking technology, which has proven to provide greater security. Simple, right? As it stands, the greatest problem facing this shift in intelligence to the edge is that there are, at the moment, very few companies creating programmable devices for the edge. It’s a different way of approaching data transmission and security, and so far, the industry has been slow to catch on: rather than trying to build a wall in front of a massive door (the Cloud), eliminate the door and create a series of constantly moving mouse holes (the Edge). Which sounds easier to protect?
Seismic Shift in IIoT Monitoring
There’s been a seismic shift in monitoring earthquakes via the Industrial Internet of Things (IIoT) with advanced Machine-to-Machine (M2M) technology have reshaped the industrial communication industry. Every device or machine along the network, even at the outermost edge, now has the opportunity to be fully-connected for automated collection and delivery of information. As Sensor-2-Server (S2S) communication technology evolves to keep up with the demand for this connectivity paradigm, new efficiencies are created and Big Data is available to drive actionable intelligence. Seismic Shift Data that Saves Lives The sheer quantity of available data, combined with the speed of automation can support mission critical applications that are designed to save lives. Research centers can leverage IoT networks to relay critical data in real-time from areas where earthquakes are a common threat to people living nearby. While natural events like earthquakes and volcanos are not avoidable or fully predictable, an IoT network can potentially help reduce the level of devastation through close, reliable seismic monitoring via highly sensitive and advanced sensor technology. S2S communications monitor and send data from remote areas where Earth changes are first detected, to the monitoring authorities who are closely tracking seismic activity. S2S solutions leveraged for early detection of these events can enable authorities to warn citizens in advance to take appropriate precautionary measures. When robust, rapid, real-time monitoring is combined with effective emergency communications, human casualties can be significantly decreased. Seismic Shift and the Ever Changing Landscape IoT has been adopted at such a rapid pace that the demand for modern, sophisticated communication technology is driving constant changes in remote, industrial communication networks that will further advance applications like seismic monitoring. These changes have clearly disrupted the traditional Supervisory Control and Data Acquisition (SCADA) market. While SCADA systems are not obsolete, industries like environmental monitoring will continue to leverage new technologies designed to help seismologists make more informed decisions than with just SCADA alone. Now, network operators can evolve and adapt their monitoring programs over time through the IoT with edge devices that allow third-party software applications to be deployed network-wide. This has not only opened new doors for software developers, but it opens up the opportunity for advancements in environmental monitoring to further improve natural event monitoring. Fast and accurate data transport from the sensor networks in seismic monitoring therefore requires robust and reliable technology that doesn’t fail in remote and sometimes harsh environments. RF technology, for example, is advancing to help field crews make intelligent decisions and closely monitor the elements that can help delivery early warning for natural events. Find us at JavaOne this Week
Top Industrial IoT News Roundup
There is a lot happening in the industrial IoT (IIoT) space lately, as evidenced by all the recent news announcements, analyst insights and business transactions occurring on the daily. Some say there is a foggy forecast for the industrial internet of things, mainly because the success of cloud computing must extend beyond data centers, but real world use cases should continue to pave the way. In some respects, perhaps it’s just the fact that the ROI from the IIoT is still in its infancy, but many are clamoring that a more standardized infrastructure is needed to help solve the unique complexities that IIoT presents. In this week’s IIoT news roundup, you’ll find a little bit of everything – from oil and gas and manufacturing to fog computing, drones and sensors. Dive in and see if you have any other articles that you think are worth adding! And don’t miss the bonus update at the end of the news roundup. Deloitte: End-to-End Automation Real Value of IIoT Technology By @KarenBoman | Published on @Rigzone “Industrial Internet of Things (IIoT) technologies such as machine learning and drones are now available, but the real value lies in linking these technologies together to allow for end-to-end automation, a Deloitte executive told attendees at the Internet of Things Oil and Gas Conference 2016 Wednesday in Houston.” Is Now the Time to Apply Fog Computing to the Internet of Things? By Dr. Vladimir Krylov @Artezio | Published on @IoTEvolution “With fog computing, latency is minimized if one uses fog nodes for data analysis without sending it to the cloud. All event aggregation in this case has to be performed in the distributed architecture deployed in the network where devices (sensors) and fog nodes are located. Thus, fog architecture moves the capacity question from the cloud to the network implementation.” Manufacturing firms investing in IIoT data analytics – even if other areas are slowing down By @James_T_Bourne | Published on @IoTTechNews “The research, the findings of which appear in the report ‘Data’s Big Impact on Manufacturing’, found that of the more than 200 North American manufacturing executives polled, 70% said investing in data analytics would lead to fewer equipment breakdowns, while less unscheduled downtime (68%), unscheduled maintenance (64%), and fewer supply chain management issues (60%) were also cited.” Go Ahead, Fly a Tiny Drone. The Man Doesn’t Have to Know By @luxagraf | Published on @WIRED “THE WILD WEST days of drone flight came to end earlier this year when the FAA began requiring that pilots register their aircraft with the agency. If you want to use your Unmanned Aircraft System (as the FAA calls them) for anything remotely commercial, you’ll need to go a step further and pass a test.” Could Optical Fibre Sensors Save Lives? By @loctier | Published on @euronews “This edition of Futuris looks at how optical fibre sensors could help monitor the stability of roads, buildings, bridges and other constructions – and save lives.” Discovering Value in the Age of IIoT By @lasher64 | Published on @automationworld “The solutions of tomorrow will be much more integrated between implementation tiers on the plant floor to the enterprise and beyond. Therefore, it is imperative that these solutions give strong consideration to network architectures and cybersecurity. As we continue to move forward, you will hear more about operational technology (OT).” IoT is not about radios; it’s all about data By Alan Carlton | Published on @NetworkWorld “The initial challenge for the Internet of Things (IoT) was how to provide physical connectivity of small and often remote devices to the Internet. This issue has basically been solved with the plethora of wireless connectivity solutions. The real challenge for IoT is data organization, sharing and search on an unprecedented scale.” BONUS NEWS This week, FreeWave announced a contest at a chance to win FreeWave’s award-winning WavePro WP201 shorthaul and Wi-Fi solution. Contest entrants must provide a high-level account of the application of the WavePro, along with a description of the need for the platform. Winners will be announced at the close of the entry period. To enter the contest, please visit: http://go.freewave.com/wavepro-network-giveaway. Submissions are due by September 30!
Top News: IoT Rules at Mobile World Congress (MWC)
After a week of everything mobile, at least in Barcelona at the Mobile World Congress (MWC), it is only fitting this week’s top news recap focuses on the other three letter acronym so hotly discussed from the show – IoT. Whether you have been living under a rock or just hadn’t embraced the fascination with the latest handheld smart technologies and cellular networking, this week’s Mobile World Congress (MWC) presented by GSMA, brought together around 800 mobile operators from more than 250 companies from around the globe to discuss the latest products, software and innovations that will push the IoT space even further into maturity. Some of the key themes to come out of this year’s MWC were the fifth generation wireless systems or 5G, the impact this next-gen tech and mobile will have on the Internet of Things (IoT) and the booming IoT businesses laying the foundations of the connected world. Now as you nestle up to your favorite mobile device or smart tablet, relax and dive into this week’s IoT news roundup from MWC! MWC: 5G Key to unlocking IoT … Just Not Yet (IndustryWeek) As the MWC surged forward with excitement for 5G to finally unlock IoT, experts warn the connective battle isn’t over, as the world dives into incorporating 5G throughout. Agence France-Presse with Industry Week reports that, “5G is the term on everyone’s lips at the Mobile World Congress in Barcelona and a global race to develop it is under way.” IoT Race Heats up at MWC 2016 (RCR Wireless) The race heats up for IoT, as 2G networks scramble to find a new way to connect with the announcement of 5G at MWC 2016. “Mobile World Congress is all about the newest wireless technologies, but this year the end of an old technology is driving conversations around the Internet of Things.” This Week’s 5G Buzz Indicates IoT is Finally Kick-Starting (VentureBeat) The hot topic on everyone’s mind this week had to be 5G and the need for more IoT connectivity. Leon Hounshell, with Greenwave Systems reminds us that, “Regardless of the hype, CES and MWC do not reveal an IoT revolution, but they certainly show us a determined evolution, where devices will unceasingly become more connected, open, and smart.” Mobile World Congress: Internet of Things Business is Humming (USA TODAY) This week may have shown us a lot of shiny new IoT products for consumers, but the truth is IoT for business will really dominate deal-making. USA TODAY believes that, “It’s not hard to see why. Gartner forecasts that the market for IoT services will top $101 billion this year, nearly 30% more than the $78 billion that businesses spent last year. By 2020, spending for services like network deployment, operations management and data analytics is forecasted to balloon to $257 billion.” Mobile World Congress: Why Every Brand Should Become a Tech Brand (Campaign Live) Connectivity is everything, and moving forward in this technological age the MWC believes all companies should become a tech brand in order to incorporate IoT. Natalie Bell with Campaign Live states that, “We are now in an era of connecting everyone and everything. So, while Mark Zuckerberg is urging us to focus on the former and ensure wider basic connectivity across the entire globe, there’s a huge tech focus on the latter — the Internet of Things, which will be greater enabled by the increasing capacity in 5G. It’s this vast array of connected objects that have caught my attention this year.”



